The Knowledge Centre

Password Security—The Benefits of Multi-factor Authentication
6th November 2019
We regularly preach (and practice!) about how important password complexity is. After all, it's in our own best interest that our clients’ systems and applications aren’t easily broken into. So, while we strongly encourage strong password security—your password by itself might not matter as much as you think.
Password managers are being used more and more, which take away the need to remember anything, let alone fear of complexity – none of us at Southern IT know a single password for any of our business or personal logins, because we just simply don’t need to and it makes life so easy in terms of abiding by ‘modern day password rules’.
Some of the most common password security rule we hear are:
- “Never use a password that has ever been seen in a breach”
- “Use really long passwords”
- “Don’t use your pets name and date of birth”
- “Passphrases are safest”
Unfortunately, by focussing on password rules, we get distracted and don’t focus on one thing that can actually make a difference, which is multi-factor authentication. Because here’s the thing:
When it comes to complexity and length, your password (mostly) doesn’t matter!
To preface this next section, we want to make it very clear that a password must still be complex in order to cover as many angles as possible. But it isn’t a one-fix-solves-all, and here’s why: You WILL give the hacker your password, without even realising it!
The below image shows you the many techniques used by cyber criminals to compromise password security and render your complex passwords useless, without you even realising.
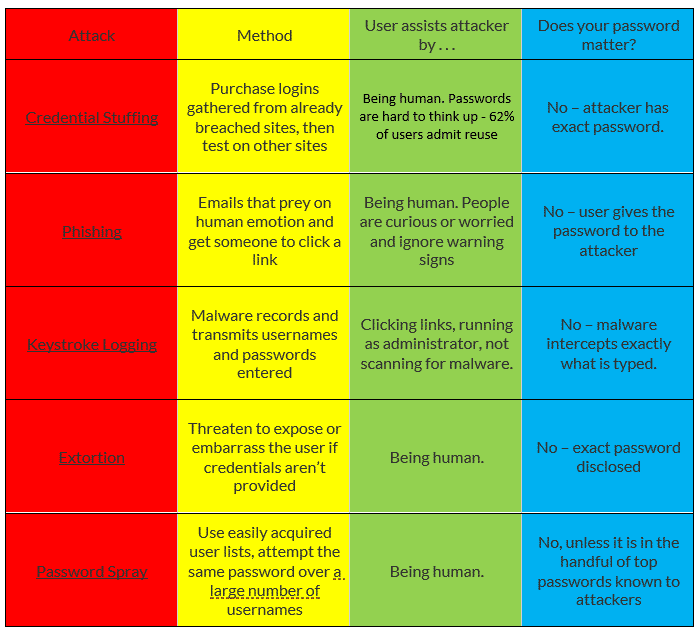
Let’s look at an example based on one of the threats in the table above:
An email arrives in an employee’s inbox. It’s a password reset for Microsoft 365 and the staff member clicks the link, enters their login details and then nothing further happens. All seems harmless and genuine. Unbeknown to the staff member, they just allowed a keystroke logger into the system. This is a type of malware that will record all keyboard entries typed (even irrelevant ones) and report back to base. The criminal will then use software that sifts through all data and pulls together a list of the username and password logins for all sites and applications accessed over a certain time period.
So, as you can see, everything you have learned about password security and having the most complex password in the world, won’t help in this scenario, as the exact letters/numbers/symbols etc, will be given to the attacker.
This is where MFA comes in.
The benefits of multi-factor authentication
Other than being vigilant towards threats such as phishing emails and ensuring your staff are regularly trained (trained, trained, and trained again!) 88% of data breaches are caused by human error. So, the best password security you can employ is multi-factor authentication. MFA requires more than one login credential in order to grant the user access. As well as your password, you will need an additional code usually sent to your phone via text or an application such as Google Authenticator, to successfully log in.
MFA will stop 99.9% of the attacks listed above. In our example, even though the hacker would have the employees’ login information, they still would not be able to access their accounts because MFA would shut them out. They wouldn’t be able to login without the code that is sent to your employee's phone.
Important – MFA isn’t unbreakable, but you have to be physically targeted in order for it to hold much risk. It’s very time consuming for the attacker and therefore they need to know it's worth it. Majority of attacks aren’t targeted, users simply get caught up in ‘volume-based attacks’ where the criminal sends out thousands of emails at once, in the hope that statically some people will click.
Boost your protections with Southern IT
The bottom line is: password security is important, but your password on its own doesn’t matter. MFA does! Based on studies, your account is more than 99.9% less likely to be compromised if you use MFA. The benefits of Multi-factor Authentication speak for themselves.
At Southern IT, we have deep experience in helping our clients fortify their defences. If you’d like to learn more about password security, the benefits of Multi-factor Authentication or how to boost your cyber security posture, get in touch with our friendly team or learn more about our cyber security services below.
Keen to learn more? Explore our other resources on Connectivity Solutions below:
- Is Your Password Secure Enough?
- Email Spoofing Scenario
- Phishing/Ransom Attack Scenario, What Would You Do?
- How to protect your business from hackers
- What is an SSL certificate and why do I need one?
- What is the Difference Between Penetration Testing and Vulnerability Scanning?
- Principles of GDPR compliance and the Rights of Data Subjects
View More Articles
Other Articles
Take a look at our most recent articles
-
- Setup a Staff Rota Using Microsoft 365 February 25, 2019 Continue reading...
- Buyer's Guide: How To Choose An IT Partner July 28, 2021 Continue reading...
Can your business recover from Disaster?
Do you have a backup? is it sufficient? when did you last review it, or test it?
Download our free 25 point checklist to help give you peace of mind that you've got the best system in place for your business needs.

